Security challenges in the cloud represent a significant hurdle for organizations migrating to or operating within cloud environments. The distributed nature of cloud infrastructure, coupled with the reliance on third-party providers, introduces a complex web of potential vulnerabilities. From data breaches and insider threats to sophisticated attacks like ransomware and denial-of-service, the landscape is constantly evolving, demanding proactive and adaptive security strategies.
This exploration delves into the multifaceted nature of cloud security threats, examining common attack vectors, mitigation techniques, and the critical role of compliance and proactive risk management. We will consider both technical safeguards and the importance of human factors, such as security awareness training and robust access control policies, in establishing a robust security posture.
Data Breaches and Leaks
Data breaches in cloud environments represent a significant threat to organizations of all sizes. The interconnected nature of cloud services, coupled with the increasing volume of sensitive data stored online, creates a larger attack surface and amplifies the potential consequences of a successful breach. Understanding the common causes, impacts, and mitigation strategies is crucial for effective cloud security.
Data breaches in cloud environments stem from a variety of factors, often involving a combination of human error and sophisticated cyberattacks. These causes range from simple misconfigurations of cloud security settings, allowing unauthorized access, to more complex attacks exploiting vulnerabilities in applications or infrastructure. Insider threats, where malicious or negligent employees compromise data, also pose a considerable risk. Phishing attacks targeting employees to obtain credentials, and the exploitation of software vulnerabilities (zero-day exploits) are other significant contributors. Finally, inadequate access control policies and a lack of robust monitoring and detection systems leave organizations vulnerable.
Impact of Data Breaches
The impact of a data breach extends far beyond the immediate loss of data. Financially, organizations face significant costs associated with incident response, legal fees, regulatory fines (like GDPR penalties), and the potential loss of customers. Reputational damage can be equally devastating, leading to a loss of customer trust, decreased brand value, and difficulty attracting investors or partners. In extreme cases, data breaches can even lead to business failure. The cost of a data breach varies greatly depending on factors like the volume of data compromised, the sensitivity of the information, and the effectiveness of the organization’s response. For instance, a breach involving customer financial data will likely result in far higher costs than a breach involving less sensitive information.
Hypothetical Data Breach Scenario and Mitigation
Imagine a mid-sized e-commerce company, “Retail Solutions,” experiences a data breach due to a misconfigured cloud storage bucket. Sensitive customer data, including names, addresses, credit card numbers, and purchase history, is exposed. The breach is discovered after a security researcher alerts Retail Solutions.
To mitigate the impact, Retail Solutions should immediately:
- Contain the breach by securing the misconfigured bucket and reviewing all other cloud storage configurations.
- Notify affected customers and regulatory bodies as required by law (e.g., GDPR).
- Launch a thorough forensic investigation to determine the extent of the breach and identify the root cause.
- Collaborate with cybersecurity experts to implement remediation measures, including patching vulnerabilities and enhancing security controls.
- Offer credit monitoring services to affected customers.
- Review and improve internal security policies and employee training programs.
Types of Data Breaches and Severity
| Breach Type | Cause | Impact | Mitigation Strategy |
|---|---|---|---|
| Insider Threat | Malicious or negligent employee actions | Data theft, reputational damage, regulatory fines | Background checks, access control policies, employee training, data loss prevention (DLP) tools |
| Phishing Attack | Malicious emails or websites tricking employees into revealing credentials | Account compromise, data theft, malware infection | Security awareness training, multi-factor authentication (MFA), email filtering |
| Cloud Misconfiguration | Improperly configured cloud services or storage | Data exposure, unauthorized access | Regular security audits, infrastructure as code (IaC), automated security configuration tools |
| SQL Injection | Exploiting vulnerabilities in database applications | Data theft, database manipulation | Input validation, parameterized queries, web application firewalls (WAFs) |
Account Hijacking and Credential Stuffing
Account hijacking and credential stuffing represent significant threats to cloud security, compromising user accounts and potentially leading to data breaches and other malicious activities. These attacks exploit vulnerabilities in password security and authentication mechanisms, highlighting the need for robust security practices. Understanding the methods employed and implementing effective preventative measures is crucial for mitigating these risks.
Account hijacking involves gaining unauthorized access to a user’s account, while credential stuffing leverages stolen credentials from one system to attempt access to another. Both tactics are often used in conjunction, with credential stuffing providing a readily available source of usernames and passwords for hijacking attempts. The consequences can range from simple account takeover to more severe incidents, such as financial fraud, data exfiltration, and reputational damage.
Common Methods for Account Hijacking and Credential Stuffing Attacks
These attacks utilize a variety of techniques, often leveraging vulnerabilities in both user behavior and system security. Phishing emails, for example, can trick users into revealing their credentials. Weak or reused passwords are easily cracked through brute-force attacks or readily available lists of compromised credentials. Furthermore, malware can silently capture keystrokes, recording usernames and passwords as they are typed. Exploiting known vulnerabilities in applications or systems can also provide attackers with direct access to user accounts. Finally, social engineering techniques can manipulate users into providing access or revealing sensitive information.
Strategies for Strengthening Password Policies and Implementing Multi-Factor Authentication
Robust password policies are fundamental in preventing account hijacking and credential stuffing. These policies should mandate strong, unique passwords, regularly updated, and of sufficient length and complexity. For instance, a policy might require passwords to be at least 12 characters long, containing uppercase and lowercase letters, numbers, and symbols. Regular password rotation and the prohibition of password reuse across different accounts are also vital. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app or security token. This significantly increases the difficulty for attackers to gain unauthorized access, even if they obtain a user’s password. Implementing MFA across all critical accounts is a highly effective defensive measure.
The Role of Security Awareness Training in Preventing These Attacks
Security awareness training plays a crucial role in mitigating the risks associated with account hijacking and credential stuffing. Educating users about the tactics employed by attackers, such as phishing emails and social engineering techniques, empowers them to recognize and avoid these threats. Training should cover best practices for password management, including the importance of strong, unique passwords and the dangers of password reuse. It should also highlight the benefits of MFA and encourage its use where available. Regular security awareness training, including simulated phishing campaigns, can significantly improve user awareness and reduce the likelihood of successful attacks.
Responding to an Account Hijacking Incident
Responding effectively to an account hijacking incident requires a structured approach. The following steps Artikel a recommended response plan:
- Identify and Contain the Breach: Immediately change all affected passwords and notify relevant parties. Disable compromised accounts to prevent further access.
- Assess the Damage: Determine the extent of the compromise, identifying any data that may have been accessed or exfiltrated.
- Investigate the Root Cause: Analyze the attack to understand how it occurred and identify any vulnerabilities that need to be addressed.
- Remediate Vulnerabilities: Patch any identified security vulnerabilities and strengthen security controls to prevent future attacks.
- Monitor and Prevent Recurrence: Implement enhanced security measures, such as MFA and advanced threat detection, to prevent similar incidents from happening again.
- Report the Incident: Depending on the severity and nature of the breach, report the incident to relevant authorities and affected individuals.
Denial-of-Service (DoS) Attacks
Denial-of-service (DoS) attacks represent a significant threat to cloud services, aiming to disrupt the availability of resources by overwhelming them with malicious traffic. These attacks can range from simple flooding techniques to sophisticated, distributed assaults, significantly impacting the performance and reputation of cloud providers and their clients. Understanding the various types, vulnerabilities, and mitigation strategies is crucial for effective cloud security.
DoS attacks flood a target system with traffic, making it unavailable to legitimate users. The impact on cloud services can be devastating, leading to service outages, financial losses, reputational damage, and compromised user experience. The severity depends on the scale and sophistication of the attack, as well as the resilience of the targeted cloud infrastructure.
Types of DoS Attacks
DoS attacks manifest in various forms, each employing different methods to disrupt service. Understanding these variations is essential for effective defense.
- Volumetric Attacks: These attacks flood the target with massive amounts of traffic, consuming bandwidth and overwhelming network resources. Examples include UDP floods, ICMP floods, and HTTP floods.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols to disrupt communication. Examples include SYN floods, which exploit the TCP three-way handshake, and Smurf attacks, which amplify traffic by using network broadcast addresses.
- Application Layer Attacks: These attacks target specific applications or services running on the cloud infrastructure, overwhelming their processing capacity. Examples include HTTP floods targeting web servers and slowloris attacks, which slowly consume server resources.
- Distributed Denial-of-Service (DDoS) Attacks: These are amplified versions of DoS attacks, leveraging a network of compromised devices (botnets) to launch a significantly larger and more powerful assault. DDoS attacks are much harder to mitigate due to their distributed nature.
Vulnerabilities Exploited in DoS Attacks
Several vulnerabilities can be exploited to launch successful DoS attacks. Addressing these weaknesses is paramount for improving cloud security posture.
- Lack of sufficient bandwidth: Insufficient network bandwidth can be easily overwhelmed by a large volume of malicious traffic.
- Weak network security configurations: Inadequate firewalls, intrusion detection/prevention systems (IDS/IPS), and other security measures can leave cloud services vulnerable.
- Unpatched systems: Outdated software and unpatched vulnerabilities can be exploited to amplify the impact of DoS attacks or even facilitate new attack vectors.
- Lack of rate limiting: Absence of mechanisms to control the rate of incoming requests can allow attackers to easily saturate system resources.
- Open ports and services: Unnecessary open ports and services provide additional attack surfaces for DoS attacks.
Mitigation Strategies for DoS Attacks
Effective mitigation strategies require a multi-layered approach, combining preventative measures with reactive responses.
- Network-level mitigation: Implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and content delivery networks (CDNs) to filter malicious traffic and block known attack sources.
- Application-level mitigation: Implementing rate limiting, request filtering, and input validation to prevent application-layer attacks.
- Cloud provider services: Utilizing cloud provider-specific DDoS protection services, which often provide advanced mitigation capabilities.
- Regular security audits and penetration testing: Identifying and addressing vulnerabilities before attackers can exploit them.
- Incident response plan: Developing and regularly testing an incident response plan to quickly contain and mitigate DoS attacks.
Implementing Traffic Filtering and Rate Limiting
Traffic filtering and rate limiting are crucial techniques for mitigating DoS attacks. They involve selectively blocking or throttling incoming traffic based on predefined rules.
Traffic filtering involves inspecting network traffic and blocking malicious packets based on source IP addresses, ports, protocols, or other characteristics. Rate limiting involves restricting the rate of incoming requests from a single source or a group of sources, preventing attackers from overwhelming the system. These techniques can be implemented using firewalls, load balancers, and application-level gateways. For example, a firewall rule might block all traffic from a known malicious IP address range, while a load balancer might limit the number of requests per second from a specific client. Effective implementation requires careful configuration and ongoing monitoring to adapt to evolving attack techniques.
Misconfigurations and Vulnerabilities: Security Challenges In The Cloud
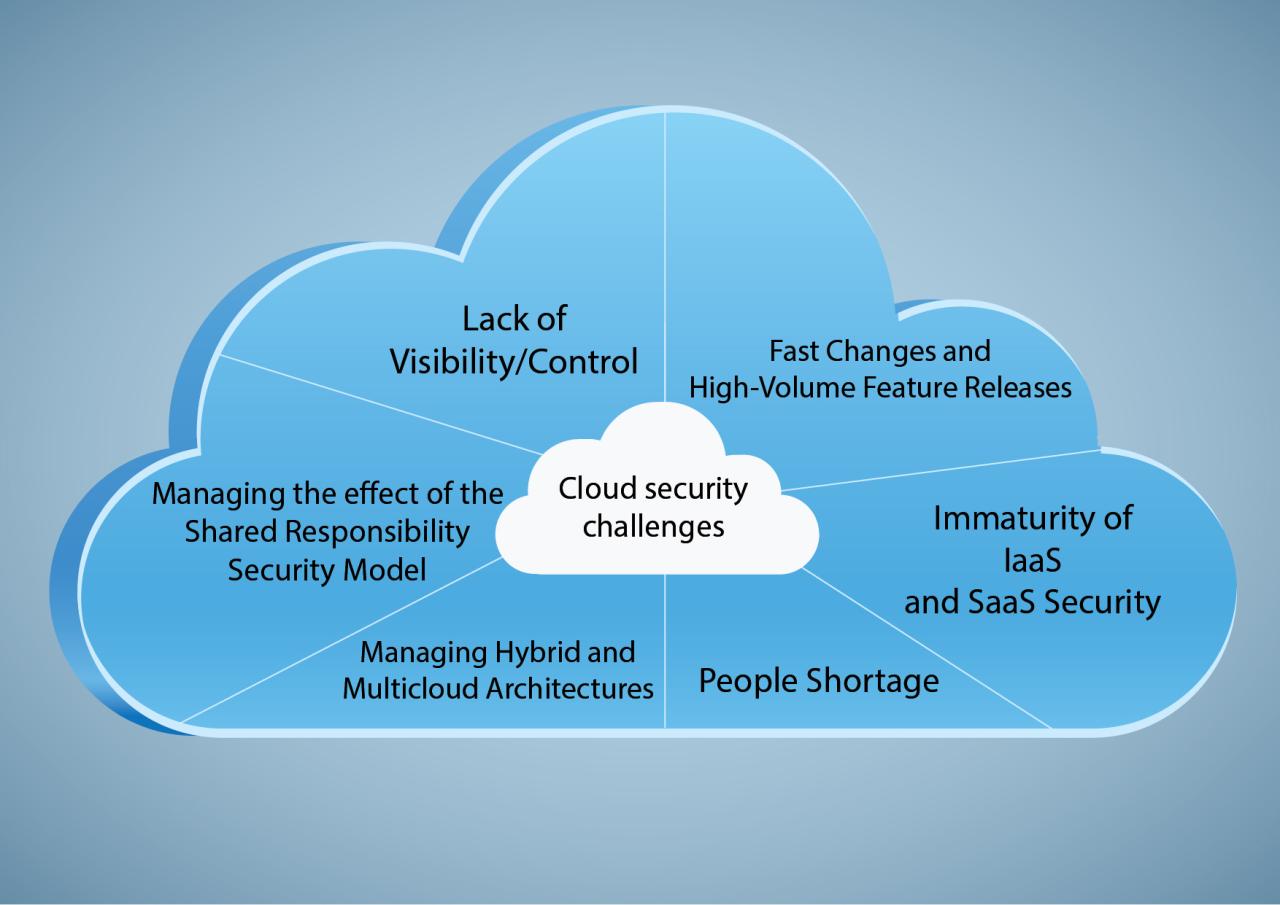
Cloud misconfigurations represent a significant security risk, often unintentionally opening doors for attackers. These errors in the setup and management of cloud resources can range from simple oversight to complex architectural flaws, leading to vulnerabilities exploitable for data breaches, unauthorized access, and service disruptions. Addressing these misconfigurations proactively is crucial for maintaining a robust cloud security posture.
Misconfigurations stem from various sources, including human error during initial setup, incomplete or outdated security policies, and a lack of understanding of cloud-specific security best practices. The consequences can be severe, impacting data integrity, confidentiality, and availability. Therefore, a comprehensive approach encompassing preventative measures, regular audits, and remediation strategies is essential.
Common Cloud Misconfigurations
Common cloud misconfigurations include improperly configured storage access controls (allowing public access to sensitive data), insecure network configurations (leaving ports open to unauthorized access), and weak or default passwords for administrative accounts. Failure to properly manage access keys and secrets, neglecting regular patching of operating systems and applications, and insufficient logging and monitoring capabilities also contribute to vulnerabilities. For example, leaving an Amazon S3 bucket publicly accessible can expose sensitive data to anyone on the internet. Similarly, an improperly configured virtual private cloud (VPC) can create a pathway for unauthorized network access.
Importance of Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are indispensable for identifying and mitigating cloud misconfigurations. Security audits provide a systematic review of cloud environments, comparing current configurations against security best practices and compliance requirements. Penetration testing, on the other hand, simulates real-world attacks to identify exploitable vulnerabilities. By combining these approaches, organizations gain a comprehensive understanding of their security posture and can prioritize remediation efforts. A robust security program will include both scheduled and ad-hoc audits, and penetration testing should be conducted at least annually, or more frequently depending on the risk profile.
Tools and Techniques for Identifying and Remediating Misconfigurations
Several tools and techniques aid in identifying and remediating cloud misconfigurations. Cloud providers offer built-in security tools like AWS Config, Azure Security Center, and Google Cloud Security Command Center, which provide continuous monitoring and alert on potential misconfigurations. Third-party security information and event management (SIEM) solutions can also enhance visibility and provide advanced threat detection. Automated security scanning tools can analyze cloud environments for vulnerabilities, and configuration management tools like Ansible and Chef can automate the remediation process. These tools, combined with skilled security personnel, form a robust approach to security management.
Best Practices for Securing Cloud Infrastructure
A checklist of best practices for securing cloud infrastructure includes:
- Implement the principle of least privilege: Grant users and applications only the necessary access rights.
- Regularly review and update security policies and procedures.
- Enable multi-factor authentication (MFA) for all accounts.
- Utilize strong and unique passwords, or password managers.
- Employ robust encryption for data at rest and in transit.
- Regularly patch and update operating systems and applications.
- Implement robust logging and monitoring capabilities.
- Conduct regular security audits and penetration testing.
- Utilize cloud-native security tools and services.
- Establish a strong incident response plan.
Following these best practices significantly reduces the risk associated with cloud misconfigurations, strengthening the overall security posture of the cloud environment. Proactive security measures are far more cost-effective than reactive responses to breaches.
Compliance and Regulatory Requirements
Navigating the complex landscape of cloud security necessitates a strong understanding and adherence to various compliance standards and regulations. Failure to comply can result in significant financial penalties, reputational damage, and legal repercussions. This section explores key compliance frameworks, the challenges inherent in cloud-based compliance, and best practices for achieving and maintaining compliance.
The challenges of meeting compliance requirements in cloud environments are multifaceted. The shared responsibility model, where the cloud provider and the customer share security responsibilities, can lead to ambiguity regarding compliance obligations. Furthermore, the dynamic nature of cloud services, with constant updates and changes, requires ongoing monitoring and adaptation of security controls to maintain compliance. The geographically distributed nature of cloud infrastructure also complicates compliance efforts, as different regions may be subject to varying legal and regulatory frameworks.
Key Compliance Standards and Regulations
Several key compliance standards and regulations are paramount for organizations operating in the cloud. These frameworks often overlap, requiring a holistic approach to security management. Examples include the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS), and the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM). Each standard specifies different requirements regarding data protection, access control, incident response, and other crucial security aspects. For example, GDPR focuses on the rights of individuals regarding their personal data, while HIPAA mandates stringent security measures for protected health information (PHI).
Challenges in Meeting Compliance Requirements in Cloud Environments
Achieving and maintaining compliance in the cloud presents unique challenges. The shared responsibility model, as previously mentioned, often leads to confusion regarding who is responsible for specific compliance obligations. The dynamic nature of cloud environments requires continuous monitoring and adaptation of security controls to reflect changes in services and regulations. Auditing and demonstrating compliance in a distributed cloud environment can also be complex and resource-intensive. Additionally, ensuring compliance across multiple cloud providers, if an organization utilizes a multi-cloud strategy, further complicates the process. For example, a company using both AWS and Azure must navigate the unique compliance requirements of each platform.
Best Practices for Achieving Compliance
Implementing robust security controls is essential for achieving compliance. This includes implementing strong access controls, using encryption for data at rest and in transit, regularly conducting security assessments and penetration testing, and establishing comprehensive incident response plans. Regular security audits and compliance certifications, such as ISO 27001, can provide independent verification of an organization’s security posture and compliance efforts. Moreover, adopting a strong security awareness training program for employees can mitigate risks associated with human error. For instance, implementing multi-factor authentication (MFA) for all user accounts significantly reduces the risk of account hijacking, a key requirement under many compliance standards.
Implementing Security Controls to Meet Specific Regulatory Requirements, Security challenges in the cloud
Implementing security controls requires a tailored approach based on specific regulatory requirements. For GDPR compliance, organizations need to implement robust data protection measures, including data minimization, purpose limitation, and data subject access requests. Meeting HIPAA requirements necessitates stringent controls around PHI, including access controls, encryption, and audit trails. PCI DSS compliance demands strict security measures for handling credit card information, such as data encryption and secure payment processing systems. Organizations should document their security controls and processes to demonstrate compliance during audits. For example, a detailed inventory of all data assets, along with their associated security controls, is crucial for demonstrating compliance with data protection regulations.
Supply Chain Attacks

The cloud’s interconnected nature introduces significant vulnerabilities through its supply chain. This expansive network of vendors, developers, and service providers, each with their own security postures, creates numerous potential entry points for malicious actors. Compromising a single link in this chain can have cascading effects, leading to widespread disruption and data breaches within the cloud environment.
Supply chain attacks leverage weaknesses within this network to gain unauthorized access to cloud resources. Attackers might target software components, hardware providers, or even cloud service providers themselves. Exploiting vulnerabilities in third-party software, for example, allows attackers to inject malicious code into applications used by cloud customers, granting them access to sensitive data or control over the environment. Similarly, compromised hardware could provide a backdoor into the cloud, while targeting a cloud provider directly could expose a vast number of clients.
Vulnerabilities in the Cloud Supply Chain
The cloud supply chain is vulnerable at multiple points. These include vulnerabilities in the software development lifecycle (SDLC), compromised hardware components, and inadequate security practices among vendors. A lack of transparency and visibility into the entire supply chain also hinders the ability to identify and mitigate risks effectively. For instance, a vulnerability in an open-source library used by multiple cloud applications could be exploited to gain access to many different cloud environments. Similarly, a compromised hardware component from a lesser-known supplier could provide a persistent, difficult-to-detect backdoor.
Exploiting Weaknesses in the Supply Chain
Attackers can employ various techniques to exploit weaknesses. These include injecting malicious code into software components during development, compromising hardware during manufacturing or shipping, or exploiting vulnerabilities in the cloud provider’s infrastructure. Sophisticated attacks might involve social engineering to gain access to credentials or manipulating the software update process to deploy malicious code. For example, a recent attack on a widely used software package resulted in a widespread compromise across many cloud-based services. The attackers managed to insert malicious code into the software before it was distributed, leading to a global security incident.
Mitigating Supply Chain Risks
Mitigating supply chain risks requires a multi-layered approach. This involves implementing robust security practices throughout the entire supply chain, from software development to hardware procurement. Thorough vetting of vendors, continuous monitoring for vulnerabilities, and regular security audits are crucial. Utilizing software bill of materials (SBOMs) to gain visibility into the components of software applications, and employing automated vulnerability scanning tools can significantly improve security. Furthermore, implementing strong access control measures and multi-factor authentication across the supply chain can help limit the impact of a compromise.
Best Practices for Securing the Cloud Supply Chain
Several best practices can strengthen the security of the cloud supply chain. These include:
- Conduct thorough due diligence on all vendors and suppliers, assessing their security posture and compliance with relevant standards.
- Implement a robust vulnerability management program, including regular scanning and patching of all software and hardware components.
- Utilize software bill of materials (SBOMs) to gain a complete inventory of software components and their dependencies.
- Employ strong access control measures, including multi-factor authentication, to limit access to sensitive data and systems.
- Regularly conduct security audits and penetration testing to identify and address vulnerabilities.
- Establish clear security protocols and incident response plans to address potential security breaches.
- Promote transparency and collaboration across the supply chain to share threat intelligence and best practices.
Successfully navigating the security challenges inherent in cloud computing requires a multi-pronged approach. This involves implementing robust technical safeguards, fostering a culture of security awareness, and embracing a proactive, risk-based approach to security management. By understanding the diverse threats and employing a layered security strategy, organizations can significantly reduce their vulnerability and protect their valuable data and operational continuity in the cloud.
Addressing security challenges in the cloud is paramount, given the increasing reliance on cloud services. Understanding these threats is crucial, and staying informed about the latest developments is key; for instance, exploring advancements is vital, as highlighted in this insightful article on Cloud Computing Trends Shaping the Future. This knowledge helps us proactively mitigate vulnerabilities and build more resilient cloud security strategies.
Understanding security challenges in the cloud is crucial for any organization. These challenges vary significantly depending on the deployment model chosen; a helpful resource for clarifying these differences is this comprehensive overview of IaaS, PaaS, and SaaS: Comparison of IaaS PaaS SaaS A Comprehensive Overview. Ultimately, a thorough understanding of these models is essential for effectively mitigating the inherent security risks associated with cloud computing.
