Identity and access management (IAM) is the cornerstone of modern cybersecurity, safeguarding digital assets and ensuring only authorized individuals access sensitive information. It’s a multifaceted field encompassing authentication, authorization, and the entire lifecycle of user accounts, from creation to deletion. Understanding IAM is crucial for organizations of all sizes, from small businesses to multinational corporations, as it directly impacts data security, regulatory compliance, and overall operational efficiency. This guide delves into the core principles, best practices, and future trends shaping the ever-evolving landscape of IAM.
We’ll explore various authentication methods, comparing their strengths and weaknesses, and examine different access control models like RBAC and ABAC, demonstrating their practical applications. We’ll also discuss the vital role of IAM in cloud environments and its critical contribution to meeting compliance requirements such as GDPR and HIPAA. The discussion will cover crucial aspects of IAM lifecycle management, automation, auditing, and monitoring, providing a holistic understanding of this critical security function.
Authentication Methods

Secure authentication is the cornerstone of any robust Identity and Access Management (IAM) system. It’s the process of verifying the identity of a user or device attempting to access a system or resource. A variety of methods exist, each with its own strengths and weaknesses, and the optimal choice often depends on the specific security requirements and context of the application.
Authentication methods are broadly categorized into something you know (passwords, PINs), something you have (smart cards, tokens), something you are (biometrics), and something you do (behavioral biometrics). Understanding these categories helps in evaluating the security and usability of different approaches.
Password-Based Authentication
Password-based authentication, while widely used, suffers from inherent vulnerabilities. Users often choose weak, easily guessable passwords, and password reuse across multiple accounts significantly increases the risk of compromise. Furthermore, passwords can be stolen through phishing attacks or malware. However, passwords remain a prevalent method due to their simplicity and familiarity for users. Strong password policies, including length requirements, complexity rules, and regular password changes, can mitigate some of these risks.
Multi-Factor Authentication (MFA), Identity and access management (IAM)
MFA significantly enhances security by requiring users to provide multiple forms of authentication. This typically involves combining something you know (password) with something you have (a one-time code from an authenticator app) or something you are (biometric scan). The advantage of MFA lies in its layered approach; even if one factor is compromised, the attacker still needs to overcome the others. This dramatically reduces the likelihood of unauthorized access. However, MFA can be more cumbersome for users, potentially leading to decreased usability and user frustration if not implemented carefully.
Biometric Authentication
Biometric authentication utilizes unique biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify identity. This method offers a high level of security as these characteristics are difficult to replicate or steal. However, biometric systems can be susceptible to spoofing attacks (e.g., using a fake fingerprint) and raise privacy concerns regarding the storage and handling of sensitive biometric data. Accuracy can also be affected by factors like environmental conditions or user-specific variations.
Secure Authentication Process for an E-commerce Website
A secure authentication process for an e-commerce website should prioritize user experience while maintaining robust security. A layered approach combining MFA and strong password policies is recommended. Upon registration, users should be required to create a strong password, ideally with a password manager. Login should incorporate MFA, potentially using a time-based one-time password (TOTP) generated by an authenticator app. For added security, account recovery mechanisms should be implemented, allowing users to regain access in case of forgotten passwords or compromised devices, while adhering to strict verification procedures. Regular security audits and penetration testing should be conducted to identify and address potential vulnerabilities.
Comparison of Authentication Methods
| Method | Strengths | Weaknesses | Implementation Complexity |
|---|---|---|---|
| Password-Based | Simple, Familiar | Vulnerable to brute-force attacks, easily compromised | Low |
| Multi-Factor Authentication (MFA) | High security, layered protection | Can be less user-friendly, increased complexity | Medium |
| Biometric Authentication | High security, difficult to replicate | Privacy concerns, potential for spoofing, accuracy issues | High |
IAM Security Best Practices
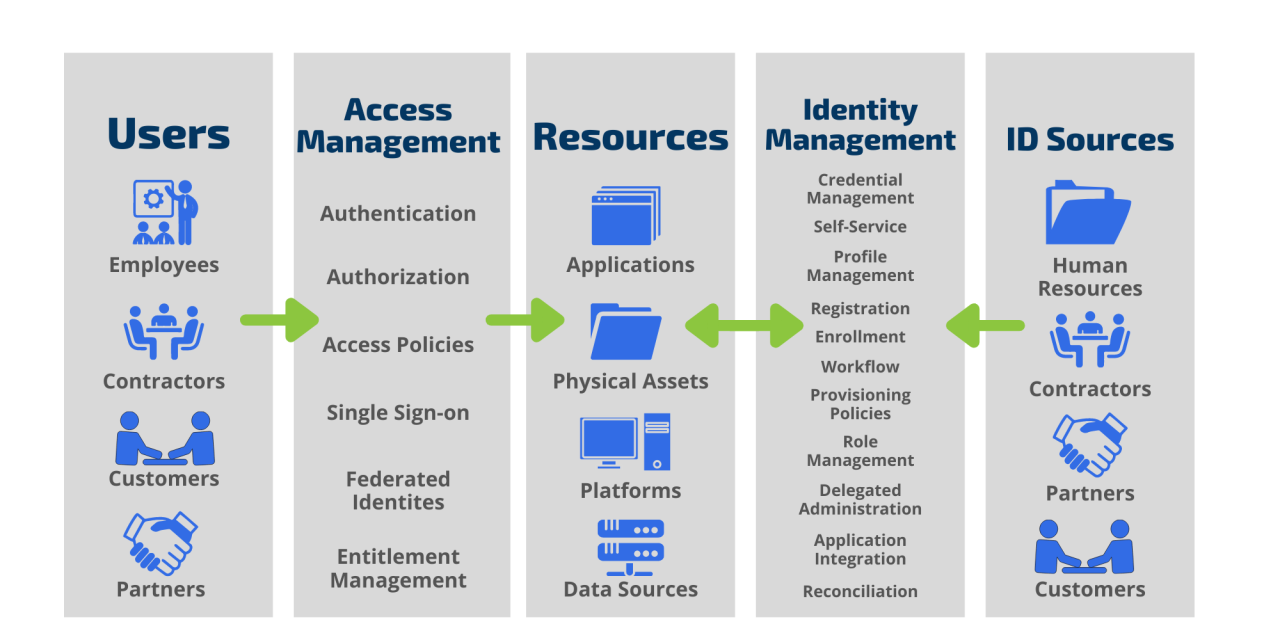
Effective Identity and Access Management (IAM) is crucial for safeguarding organizational data and systems. A robust IAM strategy requires a proactive approach to security, encompassing the identification of vulnerabilities, the implementation of preventative measures, and the establishment of ongoing monitoring practices. Ignoring these best practices can lead to significant security breaches and financial losses.
IAM vulnerabilities and security threats frequently stem from weak or compromised credentials, inadequate access controls, and insufficient monitoring. These weaknesses can be exploited by malicious actors to gain unauthorized access to sensitive data, disrupt operations, or launch further attacks. Implementing robust security measures significantly mitigates these risks, protecting valuable assets and maintaining business continuity.
Common IAM Vulnerabilities and Threats
Weak or stolen passwords represent a primary vulnerability. Phishing attacks, brute-force attempts, and credential stuffing are common methods used to obtain these credentials. Insufficient access controls, such as overly permissive permissions or a lack of role-based access control (RBAC), allow unauthorized users or applications to access sensitive data or perform critical actions. Lack of multi-factor authentication (MFA) increases the risk of unauthorized access, even if passwords are strong. Insider threats, either malicious or accidental, can also compromise IAM systems. Finally, insufficient logging and monitoring can hinder the detection of security incidents. These vulnerabilities can result in data breaches, service disruptions, and reputational damage.
Best Practices for Securing IAM Systems
Implementing strong password policies, including length requirements, complexity rules, and regular password changes, is fundamental. Enforcing multi-factor authentication (MFA) adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised. Implementing the principle of least privilege, granting users only the necessary access rights, minimizes the impact of compromised accounts. Regular security audits and penetration testing identify vulnerabilities and weaknesses before malicious actors can exploit them. Robust logging and monitoring provide visibility into system activity, enabling timely detection and response to security incidents. Employee security awareness training educates users about common threats, such as phishing and social engineering, and empowers them to protect themselves and the organization. Regularly reviewing and updating access rights ensures that permissions remain appropriate and that inactive accounts are promptly disabled.
IAM Security Checklist
Implementing a comprehensive IAM strategy requires a multi-faceted approach. The following checklist provides key security measures to consider:
- Implement strong password policies and enforce password rotation.
- Mandate multi-factor authentication (MFA) for all users.
- Utilize role-based access control (RBAC) to manage user permissions.
- Enforce the principle of least privilege.
- Regularly conduct security audits and penetration testing.
- Implement robust logging and monitoring capabilities.
- Provide regular security awareness training to employees.
- Establish a process for reviewing and updating access rights.
- Disable inactive accounts promptly.
- Regularly update and patch IAM software and infrastructure.
IAM and Compliance
Effective Identity and Access Management (IAM) is not merely a technical requirement; it’s a cornerstone of regulatory compliance across numerous industries. Failing to adequately manage access to sensitive data can lead to significant financial penalties, reputational damage, and legal repercussions. This section will explore the intersection of IAM and several key compliance regulations, highlighting how robust IAM practices contribute to meeting these requirements.
IAM significantly contributes to compliance by providing a framework for controlling access to sensitive data and systems. By implementing strong authentication, authorization, and auditing mechanisms, organizations can demonstrate their commitment to data protection and meet the requirements of various regulations. This involves not only technical controls but also robust policies, procedures, and employee training programs.
GDPR Compliance and IAM
The General Data Protection Regulation (GDPR) is a stringent data privacy regulation impacting organizations processing personal data of EU residents. GDPR mandates strong data protection measures, including data minimization, purpose limitation, and accountability. IAM plays a vital role in achieving GDPR compliance by enabling granular access control, ensuring only authorized personnel can access specific data sets, thereby minimizing the risk of data breaches and unauthorized access. Implementing multi-factor authentication (MFA), robust access reviews, and data loss prevention (DLP) tools are key aspects of an IAM strategy aligned with GDPR. For example, a company could implement role-based access control (RBAC) to ensure that only employees with a specific role, like a customer service representative, have access to customer data necessary for their job function, preventing other employees from accessing this sensitive information.
HIPAA Compliance and IAM
The Health Insurance Portability and Accountability Act (HIPAA) regulates the use and disclosure of protected health information (PHI) in the United States. HIPAA requires robust security measures to safeguard PHI from unauthorized access, use, or disclosure. IAM contributes to HIPAA compliance by providing mechanisms for authenticating users, authorizing access to PHI based on roles and responsibilities, and auditing all access attempts. This includes implementing strong password policies, regular security awareness training for employees, and rigorous access reviews to ensure only authorized personnel retain access to PHI. A healthcare provider, for instance, could use attribute-based access control (ABAC) to grant access to patient records only to authorized clinicians based on factors like their role, location, and patient relationship.
PCI DSS Compliance and IAM
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect credit card information. PCI DSS mandates strong security controls around the storage, processing, and transmission of cardholder data. IAM is critical for PCI DSS compliance, as it provides the means to control access to sensitive payment data. This involves implementing strong authentication mechanisms, regular vulnerability assessments, and strict access control policies to restrict access to sensitive payment data to only authorized personnel and systems. A retail company processing credit card payments online, for example, could utilize a dedicated IAM system for employees handling payment processing, implementing stringent access controls and regular audits to maintain compliance. This ensures that only authorized personnel have access to the sensitive cardholder data, minimizing the risk of a data breach.
IAM Tools and Technologies: Identity And Access Management (IAM)
The market offers a wide array of Identity and Access Management (IAM) tools and technologies, each with its own strengths and weaknesses. Choosing the right solution depends heavily on an organization’s specific needs, size, and existing infrastructure. Understanding the various options available is crucial for effective IAM implementation.
The selection of an IAM solution involves careful consideration of several factors, including scalability, ease of integration with existing systems, cost, and the level of security features provided. Different IAM solutions cater to diverse organizational requirements, from small businesses with basic needs to large enterprises with complex security architectures.
Types of IAM Solutions
IAM solutions can be broadly categorized into several types, each offering a unique set of features and functionalities. These categories are not mutually exclusive; many solutions incorporate elements from multiple categories.
- Cloud-based IAM solutions: These solutions are hosted by a third-party provider and accessed via the internet. Examples include AWS IAM, Azure Active Directory, and Okta. They typically offer scalability, ease of use, and automatic updates. However, reliance on a third-party provider introduces potential vendor lock-in and security concerns related to data sovereignty.
- On-premises IAM solutions: These solutions are installed and managed within an organization’s own data center. Examples include Microsoft Active Directory and CyberArk. They offer greater control over data and security but require significant upfront investment and ongoing maintenance. Scalability can also be a challenge compared to cloud-based solutions.
- Hybrid IAM solutions: These solutions combine elements of both cloud-based and on-premises solutions, offering flexibility and the ability to manage identities across different environments. This approach can be complex to implement and manage, requiring careful planning and coordination.
Feature Comparison of IAM Solutions
A direct comparison of all available IAM solutions is impractical due to their sheer number and diverse features. However, key features to consider when comparing solutions include:
- Authentication methods: Support for various authentication methods, such as passwords, multi-factor authentication (MFA), biometrics, and single sign-on (SSO).
- Authorization capabilities: Granular control over access permissions and roles, allowing for fine-grained management of user access rights.
- Identity governance and administration: Features for managing user lifecycle, provisioning, de-provisioning, and access reviews.
- Reporting and auditing: Comprehensive logging and reporting capabilities for tracking user activity and ensuring compliance.
- Integration capabilities: Ability to integrate with other security tools, such as SIEM systems, vulnerability scanners, and endpoint detection and response (EDR) solutions.
IAM Integration with Other Security Tools
Effective IAM implementation often requires integration with other security tools to enhance overall security posture. This integration can streamline security processes, improve visibility, and enable more effective threat detection and response.
For example, integrating an IAM solution with a Security Information and Event Management (SIEM) system allows for centralized monitoring of security events and logs, providing a comprehensive view of security incidents. Integration with a vulnerability scanner can help identify and remediate security vulnerabilities related to user accounts and access rights. Integration with an EDR solution can enable more effective threat detection and response by correlating IAM data with endpoint security events. These integrations significantly improve the overall effectiveness of the security infrastructure.
User Provisioning and Deprovisioning
Effective user provisioning and de-provisioning are critical components of a robust Identity and Access Management (IAM) system. These processes govern how user accounts are created, updated, and ultimately removed from an organization’s systems, directly impacting security, compliance, and operational efficiency. Inefficient or manual processes can lead to security vulnerabilities and administrative overhead.
Automated user provisioning and de-provisioning streamline account management by automating the creation, modification, and deletion of user accounts across various IT systems. This automation eliminates manual intervention, reducing the risk of human error and improving overall efficiency. The processes are typically integrated with Human Resources (HR) systems, allowing for automatic account creation upon employee onboarding and automatic account deletion upon termination. This ensures that access is granted only to authorized individuals and revoked promptly when no longer needed.
Automated User Provisioning and Deprovisioning Processes
Automated provisioning and de-provisioning leverage workflows that integrate with various systems, including HR databases, directory services (like Active Directory or LDAP), and application-specific user repositories. These systems communicate through APIs or other integration mechanisms, triggering automated actions based on predefined rules and events. For example, when a new employee is added to the HR system, the automated workflow automatically creates the corresponding user account in all necessary IT systems, assigning the appropriate roles and permissions based on the employee’s job role. Conversely, when an employee leaves the company, the workflow automatically disables or deletes the user account across all relevant systems, preventing unauthorized access. This reduces the risk of dormant accounts remaining active, a common security vulnerability.
Benefits of Automation in IAM
Automating user provisioning and de-provisioning offers significant advantages. The primary benefit is enhanced security. Automated processes reduce the likelihood of human error, which is a leading cause of security breaches. Automation also improves compliance by ensuring that access is granted and revoked in accordance with organizational policies and regulatory requirements. Furthermore, automation significantly reduces administrative overhead, freeing up IT staff to focus on more strategic tasks. Improved efficiency translates to cost savings and increased productivity. Finally, automation provides better auditability, offering a clear record of all account creation, modification, and deletion activities.
Automated Workflow for User Account Management
A well-designed automated workflow for user account management should encompass several key steps. The following bullet points Artikel a sample workflow:
- Event Trigger: The process initiates based on an event, such as a new hire in the HR system, an employee termination, or a role change.
- Data Retrieval: The system retrieves relevant user data (name, employee ID, department, role) from the HR system or other authoritative source.
- Account Creation/Modification: Based on the event and retrieved data, the system creates or modifies the user account in the directory service (e.g., Active Directory).
- Role and Permission Assignment: Appropriate roles and permissions are assigned to the user account based on their job role and responsibilities. This might involve accessing specific applications, databases, or network resources.
- Application Provisioning: The system automatically provisions access to necessary applications, either by creating accounts within those applications or updating existing accounts.
- Notification: The user and relevant administrators are notified of the account creation or modification.
- Account Deactivation/Deletion: Upon termination, the system automatically deactivates or deletes the user account across all systems, revoking access to all resources.
- Auditing: A comprehensive audit trail is maintained, recording all actions performed during the provisioning and de-provisioning process.
Future Trends in IAM
Identity and Access Management (IAM) is a constantly evolving field, driven by the increasing sophistication of cyber threats and the expanding digital landscape. New technologies and approaches are continuously emerging to enhance security, improve user experience, and streamline administrative processes. Understanding these trends is crucial for organizations to maintain robust and adaptable IAM strategies.
The future of IAM is characterized by a shift towards more automated, intelligent, and user-friendly systems. This involves a move away from traditional, password-based authentication towards more secure and convenient methods, while simultaneously addressing the growing complexity of managing identities across diverse environments, including cloud and hybrid infrastructures.
Passwordless Authentication
Passwordless authentication represents a significant paradigm shift in IAM. It eliminates the reliance on passwords, which are notoriously vulnerable to breaches and susceptible to phishing attacks. Instead, passwordless systems utilize methods such as biometrics (fingerprint, facial recognition), one-time passwords (OTPs) via authenticator apps, or FIDO2 security keys. The impact of widespread passwordless adoption would be a substantial reduction in credential stuffing attacks and a significant improvement in overall security posture. For example, Google’s adoption of passwordless authentication for its employees has demonstrably reduced security incidents related to compromised credentials.
Behavioral Biometrics
Behavioral biometrics add another layer of security by analyzing user behavior patterns, such as typing rhythm, mouse movements, and scrolling habits. This technology can detect anomalies indicative of unauthorized access, even if an attacker possesses legitimate credentials. Integrating behavioral biometrics into existing IAM systems provides continuous authentication and risk assessment, enhancing the detection and prevention of sophisticated attacks. Companies like Microsoft are already incorporating behavioral biometrics into their security platforms to improve fraud detection and account protection.
Artificial Intelligence and Machine Learning in IAM
The application of AI and ML in IAM is rapidly transforming how organizations manage identities and access. These technologies can automate tasks such as user provisioning, risk assessment, and anomaly detection. AI-powered systems can analyze vast amounts of data to identify potential threats and proactively mitigate risks. For instance, an AI-driven system could detect unusual login attempts from unfamiliar locations and automatically block them, preventing unauthorized access. This predictive capability minimizes the impact of security breaches and streamlines IAM operations.
Decentralized Identity (DID)
Decentralized Identity (DID) is an emerging approach that empowers individuals with greater control over their digital identities. Instead of relying on centralized identity providers, DID utilizes blockchain technology to create verifiable credentials that users can manage and share selectively. This approach enhances user privacy and security while streamlining authentication processes across multiple platforms. The potential impact is a more secure and user-centric digital experience, reducing reliance on large corporations to manage personal identity data. While still in its early stages, DID is showing promise in various sectors, including healthcare and finance.
Quantum-Resistant Cryptography
As quantum computing technology advances, the threat to current cryptographic algorithms increases. IAM systems need to anticipate this by transitioning to quantum-resistant cryptography, which can withstand attacks from quantum computers. This proactive measure is essential for maintaining long-term security and protecting sensitive data. The transition will require significant investment and careful planning, but the potential consequences of inaction are far greater. Several standards bodies are already working on developing and implementing quantum-resistant algorithms.
Effective Identity and Access Management is not merely a technical exercise; it’s a strategic imperative for organizations seeking to protect their data, maintain compliance, and foster a secure digital environment. By understanding the fundamentals, implementing best practices, and staying abreast of emerging trends, organizations can build robust IAM systems that effectively manage access, mitigate risks, and safeguard valuable assets. The journey towards robust IAM requires ongoing vigilance, adaptation, and a commitment to continuous improvement, ensuring that the security posture remains aligned with the evolving threat landscape and organizational needs.
Robust Identity and access management (IAM) is crucial for any organization, especially in today’s complex digital landscape. Understanding the evolving security needs is paramount, and this is deeply intertwined with the broader shifts in cloud technology, as detailed in this insightful article on Cloud Computing Trends Shaping the Future. Therefore, adapting IAM strategies to meet these emerging trends is key to maintaining a secure and efficient cloud environment.
Effective Identity and access management (IAM) is crucial for securing cloud environments. Understanding the different deployment models significantly impacts your IAM strategy; for a helpful breakdown of Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), check out this comprehensive overview: Comparison of IaaS PaaS SaaS A Comprehensive Overview. Ultimately, robust IAM practices are essential regardless of your chosen cloud model.
